Cybersecurity Strategies

Cybersecurity Strategies
Due to global interconnectedness and our increasing dependence on complex digital systems, the Global Risks Report 2022 of the World Economic Forum ranks cyber-attacks and data misuse as one of the biggest short- and medium-term global risks. These thus come before economic risks and after the environmental and social risks listed in first place. Cyber risks arise primarily from individual, human actions, but can trigger national and global conflicts, especially at government level.
People in countries of the Global South are particularly affected by cyber risks. Mobile devices susceptible to cyber-attacks are widely used here, but well-trained specialists are not always available. Often there is also a lack of appropriate sensitization. At the same time, protection and industry standards are low and regulations are insufficient. Thus, according to the Global Cybersecurity Index (2020) of the International Telecommunication Union (ITU), only a few of the African states have laws or strategies to promote cybersecurity, even if the importance of cybersecurity is often emphasized in corresponding digital agendas. According to the ITU, 37 out of 55 African countries have cybersecurity regulations and only 13 countries have a corresponding strategy.
In order to address the risks and ensure the security of the digital space, coordinated action needs to be implemented by government authorities with the involvement of the private sector and civil society. The basis for this is a comprehensive cybersecurity strategy that specifies the vision, goals, principles and priorities that guide a country in dealing with cybersecurity.
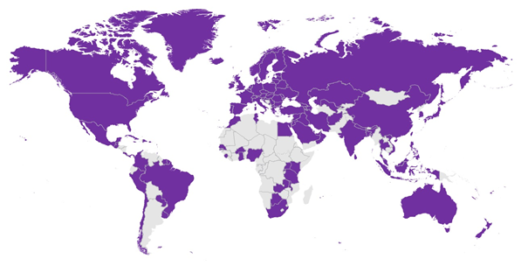
The National Cybersecurity Strategies Repository contains national cybersecurity strategies. These include single or multiple documents or are an integral part of a broader ICT or national security strategy.
A good overview of national cybersecurity strategies and their background provides UNIDIR’s Cyber Security Portal. Relevant strategy documents and implementation frameworks, national structures, legal frameworks and existing cooperations are presented for each country.
Tools for developing and evaluating cybersecurity strategies
Nevertheless, developing a cybersecurity strategy is always complex. It includes important regulations (often with interference with fundamental rights) in the legislative field, possibly the establishment of new state agencies and authorities, the planning and implementation of national campaigns and much more.
However, tools are available to help you navigate the development and evaluation of such strategies. Two of these tools will be briefly introduced here.
Guide to Developing a National Cybersecurity Strategy
The ITU published the Guide to Developing a National Cybersecurity Strategy (2021). It was developed with twelve global partners from research, the private sector, international organisations and civil society. The guide aims to provide assistance to national leaders and policymakers in developing their national cybersecurity strategy. Building on extensive experience, it provides an overview of what makes successful cybersecurity strategies. In doing so, it tries to take into account all aspects of cybersecurity (political, operational, technical and legal).
Furthermore, the guide includes overarching principles such as human rights, inclusion, resilience or building trust in the national ecosystem and presents good practices for this purpose.
The guide has already served as a basis for the development of Bhutan’s cyber strategy and for the evaluation of cyber strategies in the Caribbean, Central and South America as well as the West Balkans.
Trust4Cyber
The flagship project Trust4Cyber has set itself the goal of strengthening the skills of actors from government, privat business and civil society in the field of cybersecurity.
For example, the project carried out cybersecurity policy exercises with individual countries (Rwanda, South Africa, Kenya, Ivory Coast, Ghana, Mexico and Jordan). In preparation for this simulation game, detailed Country Profiles on the topic.
In addition, E-learning courses on international cybersecurity policy have been developed. These are available on the e-learning platform atingi free of charge.